



Feature Story
More feature stories by year:
2024
2023
2022
2021
2020
2019
2018
2017
2016
2015
2014
2013
2012
2011
2010
2009
2008
2007
2006
2005
2004
2003
2002
2001
2000
1999
1998
 Return to: 2015 Feature Stories
Return to: 2015 Feature Stories
CLIENT: PRPL FOUNDATION
September 2015: RTC Magazine
An open-source, community-driven effort is concentrating on enabling next-generation Internet of Things with portable software, virtualized architectures and reliable security.
Data center to device. That's a tall order, but that is what is implied by the ambitious phenomenon known as the Internet of Things and it is attracting huge numbers of eager participants. And there is certainly room for participation, innovation, specialization, imagination and more. There is also what might be an inherent paradox: the need for both open connectivity, i.e., public interfaces and standards, plus the need for security. We seem to want everything to be able to connect to everything else, but not necessarily allowed to connect to everything else. Here, but not for the first time, open source meets the need for security.
The prpl Foundation is a new consortium that was formed last year to meet the dual challenges of interoperability and security from the device to the datacenter. prpl has an early list of prominent companies as members, including board members Broadcom, Imagination Technologies, Lantiq (recently acquired by Intel) and Qualcomm, as well as more than a dozen other IP, SoC, security and software companies. In what might at first seem somewhat contradictory, the Foundation targets the MIPS architecture as the starting point for the development and collaboration efforts on security. But since the Foundation is open to other architectures, and the output of prpl's security working group will be open sourced, concepts developed on this and similar platforms (Figure 1) should be easily portable to other architectures. The goal is to make the security framework, architecture and APIs independent of any instruction set architecture and any particular proprietary security implementation. Members developing software for higher layers would of course not be bound to a given processor architecture.

Figure 1
The MIPS Creator CI20 platform from Imagination Technologies is a MIPS/Imagination Linux and Android development system. It incorporates an Ingenic JZ4780 SoC which includes a 1.2GHz dual core MIPS32 processor and Imagination PowerVR SGX540 GPU. The CI20 board provides comprehensive connectivity, multimedia capabilities and substantial RAM and flash. Other development platforms are expected to be available in the near future.
Activities of the prpl Foundation are driven by prpl engineering groups or PEGs, which target specific domains. Currently there are three PEGs: The QEMU, which is working on a generic and open source machine emulator and virtualizer, the prplwrt PEG, which is focused on an open source embedded Linux platform for use with such things as Wi-Fi routers and other mission-critical reliable products. Finally, there is the Virtualization and Security PEG, which has just been formed to address secure software environments across datacenter, networking, home, mobile and embedded environments—a tall order indeed.
The QEMU actually expresses the approach mentioned above. It is a generic and open source machine emulator and virtualizer. When used as a machine emulator, it can run operating systems and programs developed for one machine such as an ARM processor on a different machine, be it based on MIPS or Intel hardware. Using dynamic translation, the QEMU is able to achieve quite good performance. When used as a virtualizer, it is able to achieve near native performance because it executes the guest code directly on the host CPU.
QEMU supports virtualization when executing under the Xen hypervisor or when using the Linux kernel virtual machine (KVM) kernel module. KVM is a module that allows a user space program to utilize the hardware virtualization features of various processors. For example, it supports Intel and AMD x86 and x86_64 processors as well as PowerPC 440 and 970 and MIPS32 as well as ARM Cortex-A15 and AArch64. The goal, then, is to have an emulator that can run any code from any other platform.
The mission of the prpl working group is to enable the close cooperation of users, hardware manufacturers, semiconductor manufacturers and the broader community of OpenWrt developers. OpenWrt is an embedded operating system based on the Linux kernel and primarily used on embedded devices to route network traffic. The main components are the standard Linux kernel, util-linux, uClibc, which is a small C library intended for Linux-kernel-based embedded and mobile systems. It is intentionally much smaller than the glibc library normally used with Linux distributions. In addition to being smaller to fit embedded application needs, uClibc can have selected features deleted to meet space requirements. OpenWrt also includes BusyBox, a set of stripped-down tools for use with embedded operating systems with limited resources that can provide something over 200 utilities. OpenWrt is an existing open source project with a vibrant developer community and is widely used by SOC vendors, Wi-Fi router OEMs, and software developers as their primary embedded Linux distribution.
The newest—and most challenging—PEG project to come out of the prpl Foundation is the effort to define an open security framework for deploying secured and authenticated virtualized services. The Security PEG initially consists of Broadcom, CUPP Computing, Elliptic Technologies, Ikanos, Imagination Technologies, Imperas Software, Ingenic, Kernkonzept, Qualcomm, Seltech and others with more possibly to join.
Uniting the ideas of "open framework" and "security" will entail the job of transiting from today's software-virtualized solutions to full hardware-supported virtualization (seen here as a vital element) that will enable multi-domain security across processors, heterogeneous SoCs and systems built on them including connected devices, routers and hubs. In addition, the Security PEG will define open APIs for various levels of the security stack in an effort to introduce commonality of approach to implementing security.
The idea of hardware virtualization appears to be key to the effort. According to prpl Foundations' Chief Security Strategist, Cesare Garlati, "Security is the number one enabler of technology these days. There is no piece of technology today that does not require some security." Attacks can of course come from all sources, from teenage hackers making mischief to PhD computer scientists in a foreign government trying to take down an entire nation's power grid.
And let's be frank. There is no such thing as 100 percent security. The complexity from firmware to middleware and software from endpoint to endpoint is just too great for a single solution. So the task becomes one of risk management in what Garlati sees as the concept of layered security. "No one solution will be effectively 100 percent, but if you add more and more solutions at different layers, what you achieve becomes very close to 100 percent." Just how close that might be is, of course, going to be the subject of endless debate.
We have been assisted greatly in the task by the enormous growth in hardware performance as well as by the scales of integration that are now available to us. One fairly obvious fact is that security does affect performance as well as cost, so like any other technological issue, it is a trade-off. Garlati notes, "Now increasingly. exploding processor technology, core technology, is able to embed some of the security layers, putting multidomain security into the cores." To that must be added usability, the idea of the common API mentioned above, to let users set up security functions.
Garlati says it is unrealistic to expect high security from any complex piece of software - such as modern operating systems - even if beefed up with additional security modules. "The attack surface is simply too large," he says. Only the smallest kernel could be actually audited and an OS kernel like Linux has over 17 million lines of code, which is incredibly difficult to analyze. "Security has to be something that you boot before that kernel," he says.
With today's multicore architectures, the goal is to develop a microkernel and a hypervisor that can boot off the system itself. That way it can maintain separation between the kernel and anything you may boot on top of that. The microkernel under consideration is something like 30k bytes, which can be audited and analyzed. Then with anything you boot on top of that you can maintain separation and contain any damage from affecting any adjacent entity (Figure 2).
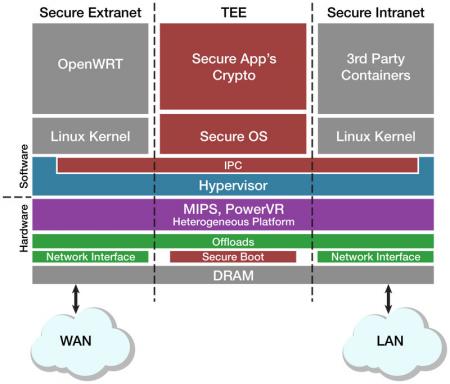
Figure 2
The goal of true separation is the basis upon which other security measures such as encryption, authentication, etc., will be built. The hypervisor enables the creation of multiple secure domains where any damage would affect only that container and not the entire system.
prpl Security and Virtualization PEG members are pursuing an ambitious goal. As hardware performance and integration increase, so does the ability to integrate security measures at the hardware level and service software security measures at higher layers. At the same time, of course, so do complexity and the ability and motivation to host multiple—often very different—services on the same system. This requires separation and security for orderly service as well as for protection against hackers. The advantage of having such basic security along with a standard model of how to implement requires industry-wide collaboration but holds the promise of greatly enhanced utility and confidence in the promise of the Internet of Things.
prpl Foundation
Santa Clara, CA
www.prplfoundation.org
Return to: 2015 Feature Stories