



Feature Story
More feature stories by year:
2024
2023
2022
2021
2020
2019
2018
2017
2016
2015
2014
2013
2012
2011
2010
2009
2008
2007
2006
2005
2004
2003
2002
2001
2000
1999
1998
 Return to: 2016 Feature Stories
Return to: 2016 Feature Stories
CLIENT: PRPL FOUNDATION
Jan. 7, 2016: The Register
Tech foundation publishes gentle guide
A 101 introduction to designing secure Internet-of-Things devices and similar systems has been published today by the MIPS-cheerleading Prpl Foundation.
The illustrated guidebook is not tied to the aforementioned processor architecture: it can be understood by anyone dabbling in ARM, x86 and MIPS-based embedded engineering.
It's aimed at people designing internet-connected gadgets and gizmos who want to make sure malicious code doesn't end up compromising devices. If you're an engineering sage, this 55-page document isn't going to flip your control register bits, but if you're new to this space, it will give you a good steer.
The free PDF focuses a lot on the software side: how to set up the underlying bootloader, operating system, apps, and hypervisor (if necessary) to ensure the right code is executed – from the firmware reset vector to the final exit() in the application. You don't want parts of the kernel or drivers swapped out for backdoored copies, for example, and so an overview of building a root-of-trust to prevent this is described.
The guidance advocates security by separation; in other words, forcing functions into their own compartments and are not allowed to interfere with each other. Software written for microcontrollers and similar resource-tight systems used in embedded engineering tends to muck everything together to keep things running fast and deterministically, which is a bit of a nightmare to secure. Modern chips, though, can split program code into walled gardens using memory protection mechanisms and hardware domains, so why not take advantage?
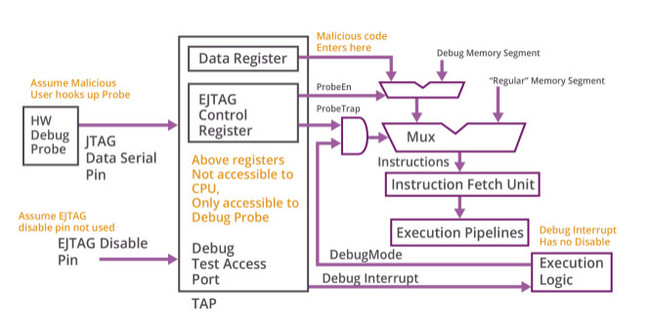
Another sticking point is debugging: how do you – the programmer – dig into the very lowest levels of a system to single step through instructions, set breakpoints, and catch bugs if the device is engineered to stop people doing that? How can products be tested to be secure, and programming blunders ironed out, in restricted environments? So suggestions are given.
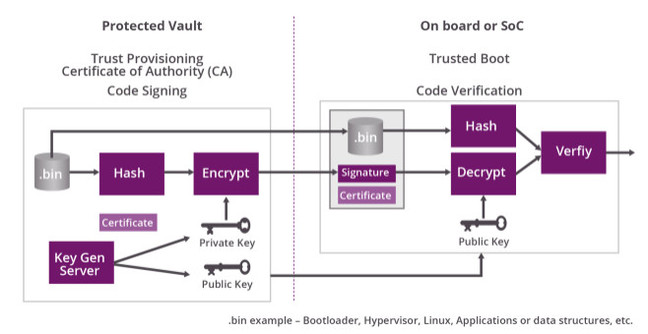
As stressed above, this is guidance: it's not a hardware reference manual, and it starts out recapping the state of Internet-of-Thing security, which may put off readers with short attention spans. The document has been peer reviewed, and its more-than-two-dozen contributors are named.
Prpl is a non-profit organization forged by Imagination Technologies to promote the MIPS architecture, although folks from rival processor clans are welcome to join. While ARM is the undisputed king in the embedded engineering world, and Intel is constantly trying to invade millimetre by millimetre, MIPS still hangs its hat on networking gear – a cornerstone of IoT.
Return to: 2016 Feature Stories